Commercial disk-wiping apps love to advertise themselves as secure, advanced, and essential. But under the hood, many of them just automate what a few native Linux commands already do—brilliantly, simply, and freely.
In this article, we’ll look at one of the most elegant, powerful ways to securely wipe free space on a Linux (or Unix-like) system. No installations. No fees. Just terminal magic:
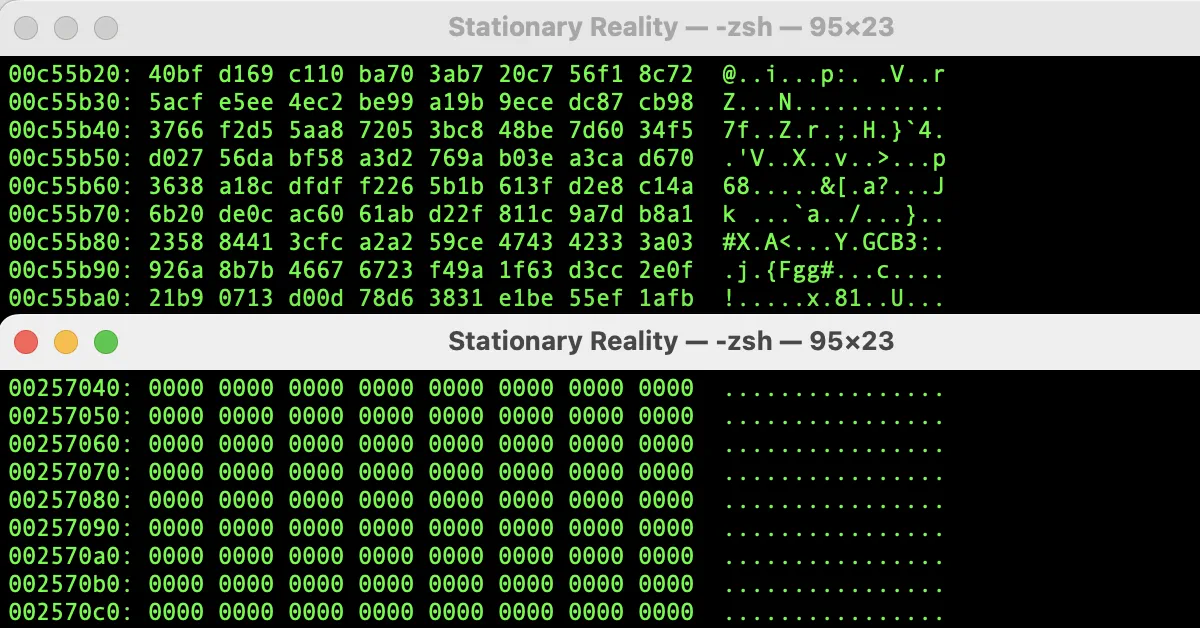
cat /dev/urandom > tmp.file
Let’s break this down, piece by piece:
🧱 The Building Blocks
cat
Stands for concatenate. It’s a standard Unix command that reads the contents of a file (or device) and outputs it tostdout. It can also redirect output to another file using>./dev/urandom
This is a virtual device—a software interface that behaves like a file, but behind the scenes, it provides a stream of pseudo-random bytes generated by the kernel’s entropy pool. It’s commonly used by programs that need random data (like cryptographic tools).>tmp.file
The>operator redirects the output ofcatto a file. In this case, all that random data is being written totmp.file, byte by byte.
🧹 Why It Works for Wiping Free Space
When you delete a file on most filesystems, only the reference to the file is removed. The raw data remains on disk until it’s overwritten.
By using /dev/urandom, you are writing meaningless, random data into a file that will fill up all available free space. This process overwrites the remnants of deleted files, rendering data recovery extremely difficult—even with forensic tools.
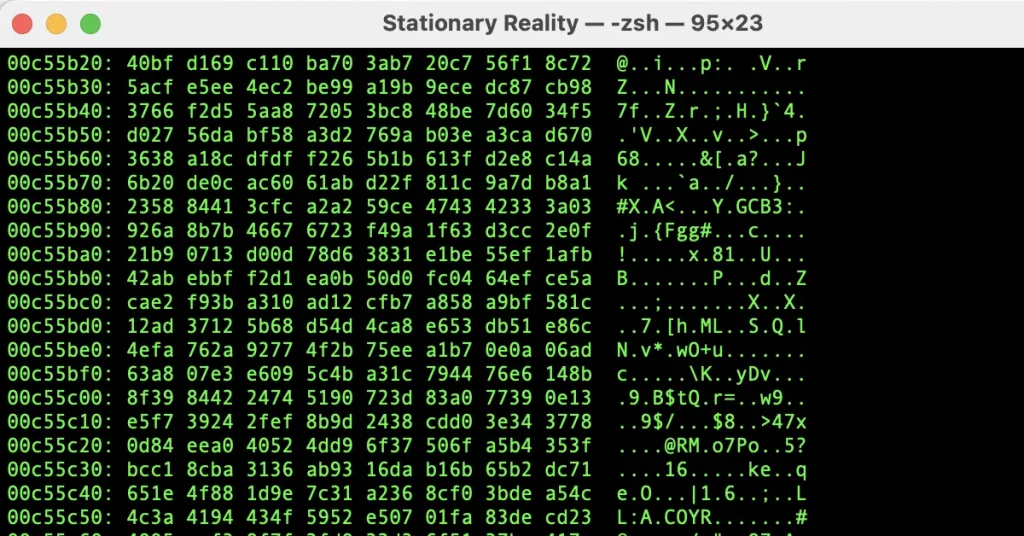
Once the space is full, you can delete tmp.file:
rm tmp.file
And your free space will now contain gibberish instead of potentially sensitive deleted data.
🧠 Bonus: Making It Compressible with /dev/zero
After filling your disk with random data, the entire free space is now effectively “dirty.” If you later want to back up your drive using a byte-for-byte method (like dd), that random data will make the image larger and less compressible.
Enter another native Linux tool:
cat /dev/zero > zero.file
/dev/zerois another virtual device, but instead of random bytes, it outputs zeroes (0x00) continuously.- Running this after wiping with
/dev/urandomreplaces random data in free space with zeros—ideal for compression tools like gzip or zstd, which can shrink long sequences of zeroes far more efficiently.
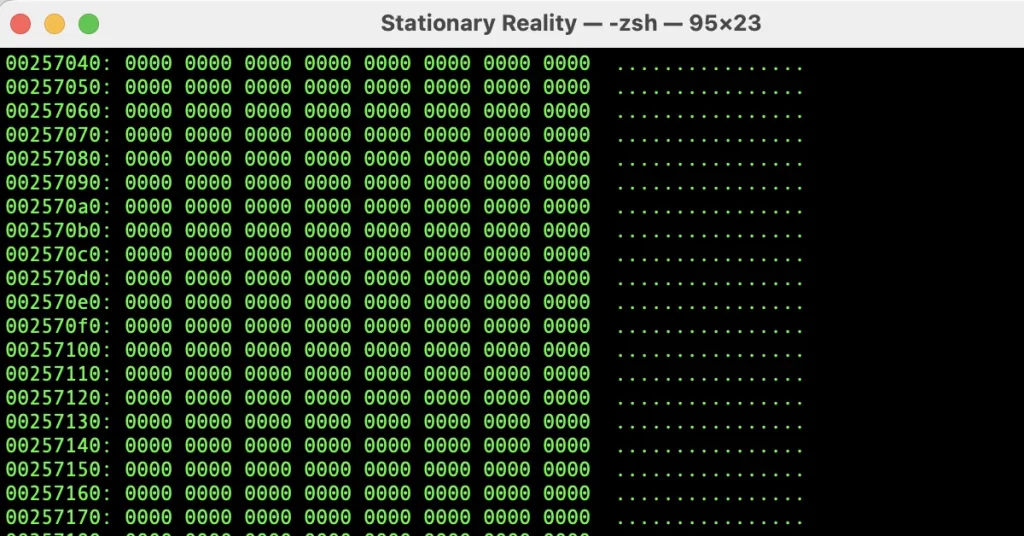
Then just delete the file again:
rm zero.file
💡 Why This Matters
This whole process is a perfect example of how Linux gives you primitive, powerful tools that work like building blocks. While commercial apps often obscure what they’re doing behind sliders and progress bars, commands like cat /dev/urandom > file make the process transparent, scriptable, and free.
This method is:
- OS-native (works on Linux, macOS, and other Unix-like systems)
- Free of external dependencies
- Secure (overwrites free space)
- Customizable
- Educating (you learn more than just clicking a “Wipe” button)
🪟 What About Windows Users?
If you’re on Windows, you have a solid option for securely wiping free space:
Use the Built-In cipher Command
Windows includes a built-in tool for this exact purpose:
cipher /w:C:\
This command writes over all free space on the specified drive (in this case, C:) with zeros. It does not delete files—only overwrites free space left by previously deleted files. It’s fast, simple, and doesn’t require any downloads.