Seeing Data on the Move
Every day, countless packets leave your device, cross dozens of networks, and return with everything from images to video calls. But what is a packet, really? Where does your image go once it leaves your machine?
This article zooms in on data in motion — how raw bytes (like a JPEG) are split, wrapped, encrypted, and sent through space… and how tools like Wireshark let us see all of it.
If hex editors are the microscope for data at rest, then Wireshark is the stethoscope for data in motion. It listens to the live stream of bits flowing in and out of your machine — and shows you every layer.
But to make sense of it, you need to understand encapsulation: the idea that each piece of data is wrapped like a nesting doll — first in application-level structure (e.g., a JPEG or HTML file), then in protocols (like TCP/IP), and finally in physical transmission.
👂 What Wireshark Does
Wireshark shows you what your computer actually sends and receives — in exquisite, structured detail.
For example, if you request an image over HTTPS, Wireshark lets you see:
- The frame your machine sent or received
- The IP addresses and ports involved
- The TCP layer that segments and reassembles the stream
- The TLS encryption wrapping your image data
- …and sometimes, the image bytes themselves
Let’s break it down using a real-world example.
🖼️ The Same Image, But In Transit
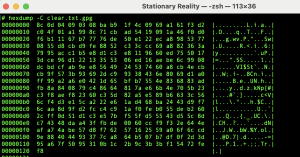
Here’s what the start of a JPEG looks like in a hex editor:
ff d8 ff e0 00 10 4a 46 49 46 00 01 01 01 00 48 ...
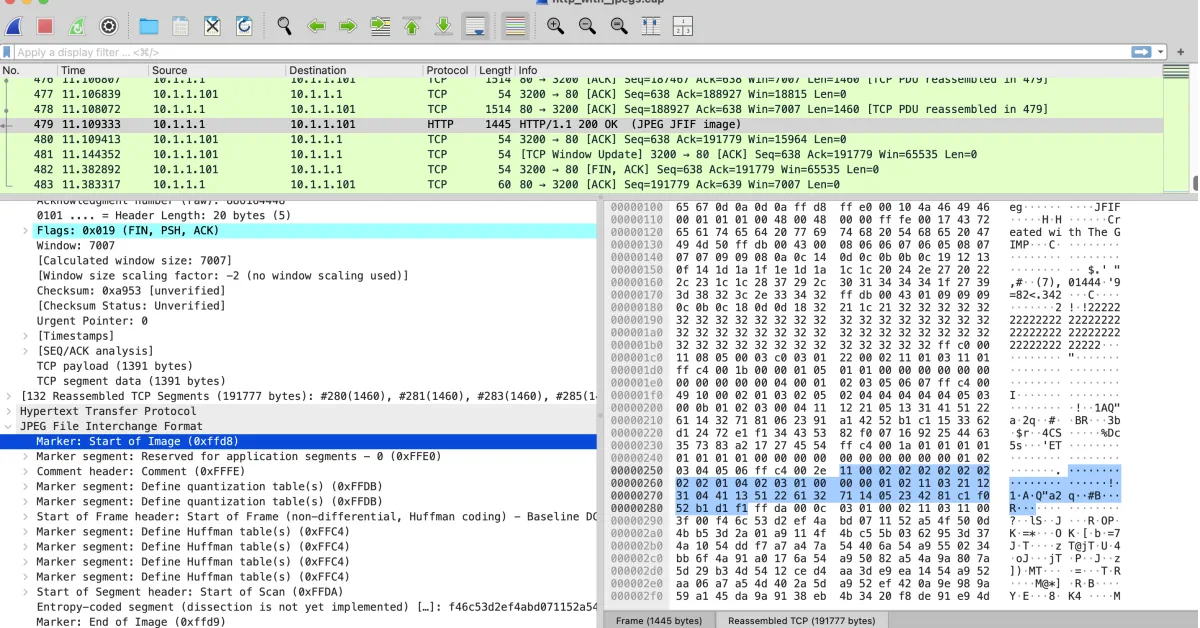
And here’s what that same data looks like when traveling over the network, as seen in Wireshark, notice how the dark blue selection on the right is the JPEG decoder and on the right side, the lighter blue highlight shows the start of the file data:
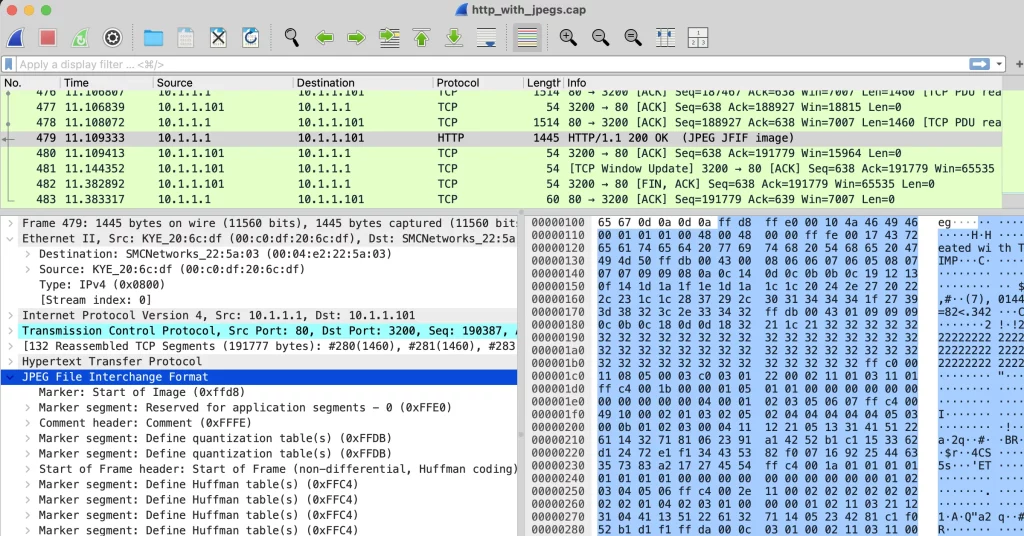
(Click image to see full size)
🪆 Encapsulation in Action (OSI Breakdown)
Each packet is wrapped in several layers, and Wireshark helps peel them back. These correspond to the OSI model, which is a helpful mental map.
🧠 Application Layer (Layer 7)
- Protocol: HTTPS
- Action: Sends a
GET /image.jpgrequest, receives a JPEG file - View in Wireshark: Might show up as
HTTP, or just encrypted TLS “Application Data”
📡 Presentation Layer (Layer 6)
- Protocol: TLS (SSL)
- Action: Encrypts your request and the image
- Note: Without TLS decryption, you can’t see raw image bytes unless the site uses HTTP.
🧭 Session Layer (Layer 5)
- Role: Coordinates communication sessions and reassembly
- Note: Usually handled invisibly inside transport protocols (like TCP)
🚚 Transport Layer (Layer 4)
- Protocol: TCP
- Action: Breaks the data into segments and tracks delivery
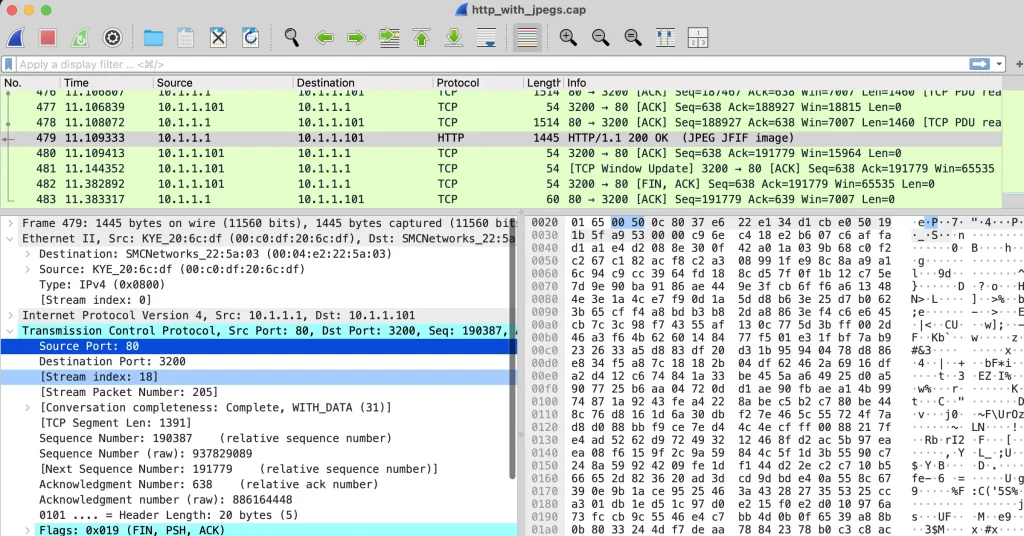
(Click image to see full size)
The purpose is to illustrate how each layer is stripped off before it is passed on to the next. In Wireshark, some fields on the left are informational, but some of them are specific sections of data being decoded. For example, I selected Source Port: 80, which is the default web port (http), if you look to the right, you will see hex 00 50. 0050 is 10100000 in binary, which is 80 in decimal.
The computer is physically sending the represented binary codes that are telling the receiving computer that it wants to communicate with it over port 80, so the operating system passes that incoming data to the proper process, which is web server software.
🌐 Network Layer (Layer 3)
- Protocol: IPv4 or IPv6
- Action: Routes data using IP addresses
- Wireshark Sample:
Src IP: 192.168.1.10
Dst IP: 151.101.1.140
TTL: 64
🔌 Data Link Layer (Layer 2)
- Protocol: Ethernet II or 802.11
- Action: Adds source/destination MAC addresses
Notice how the first part of the data frame is 00 04 e2 22 5a 03 – This is the destination MAC address of the destination computer. In other words, your network equipment will see this as it leaves the network cable and it will use it to lookup the device that it is addressed to in its lookup table. Because this is a local layer, it will always be your routers MAC address, unless you are communicating with another device in your local network.
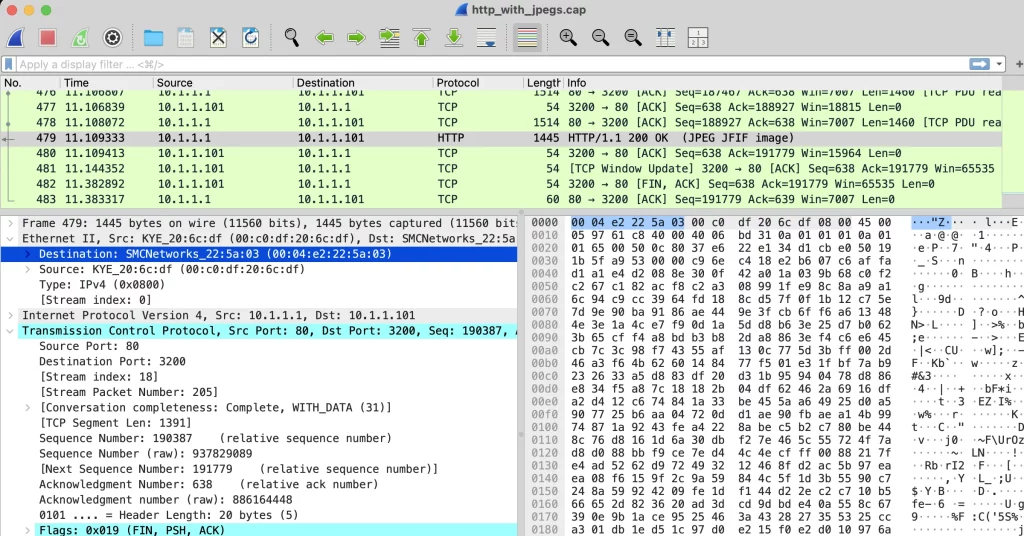
🧲 Physical Layer (Layer 1)
- Action: Turns digital bits into electrical or wireless signals
- Visible in Wireshark? Not directly — but this is what puts your packet on the wire
🧪 Putting It All Together
Wireshark reveals what you’ve already seen with a hex editor — the raw image bytes — but inside their full network wrapping:
FF D8 FF E0 00 10 4A 46 49 46 00 01 ...
This is data in motion, still perfectly structured, just wrapped in:
- TCP headers
- IP routing
- Ethernet frames
- Encrypted TLS packets
💡 Key Insight
Once you know what you’re looking at, Wireshark becomes a living hex editor — showing you how protocols wrap and unwrap data in real-time.
It demystifies what’s happening under your browser, under your apps, under your OS.
Future installments may explore HTTP headers, session cookies, or even DNS spoofing — because it’s all visible, if you know where to look.