🧪 A Simple Test: How Hidden Is Your Data?
I think the best way to talk about encryption tools is to start off with GPG. Not only is it open source and free, but it’s also:
- Actively maintained and widely used
- Available for every major OS
- A cornerstone of open cryptography
And most importantly, it’s the best way to illustrate a few key concepts in security:
- 🟩 Cleartext
- 🟨 Encoding (obfuscation)
- 🟥 Encryption
👁️ Step 1: The Cleartext
I created a simple file on my computer. It’s just a friendly message with a secret passphrase embedded inside.
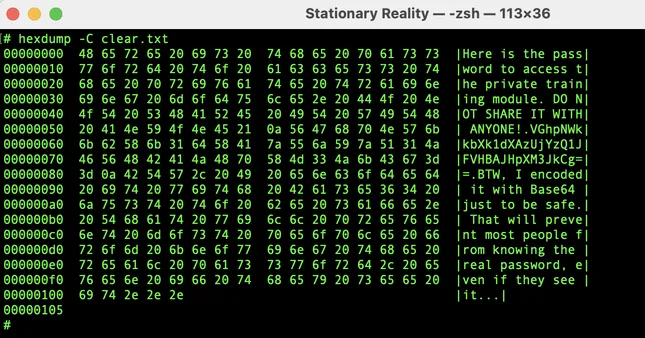
Observation:
When you view this file in a hex editor, it’s fully readable. That’s cleartext — it’s exactly what it looks like.
🎭 Step 2: Encoded, Not Encrypted (Base64)
Just to show what obfuscation looks like, here’s that same message encoded with Base64.
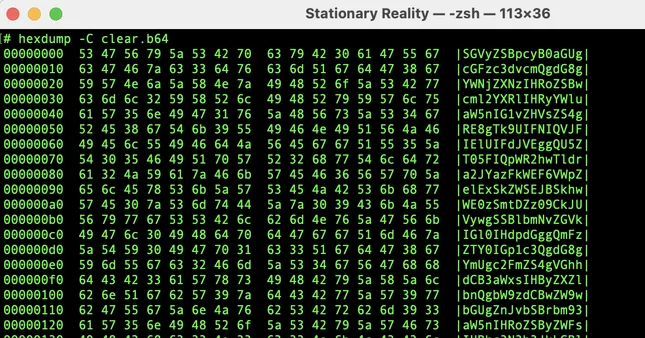
Base64 is not encryption. It’s a reversible encoding that turns binary into ASCII — useful for email or URL-safe transfer, but not secure.
A casual observer won’t read it directly — but a basic base64 -d will reveal the original message.
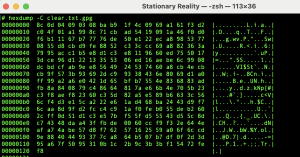
🔒 Step 3: GPG Encrypted Message
Now here’s the same message, encrypted with GPG using a symmetric passphrase.
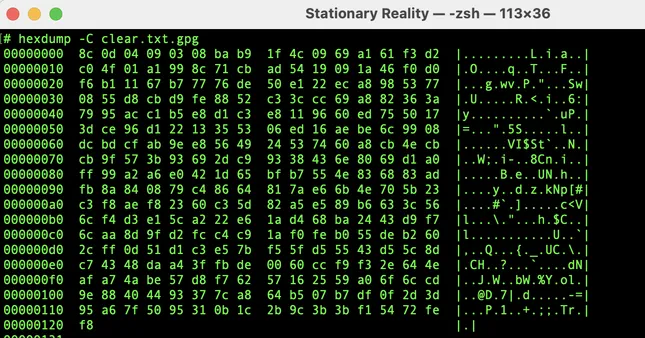
This time, the data is no longer recognizable — even when viewed as hex.
It’s not just scrambled. It’s protected.
Yes, it uses a password — and yes, the original message included another password. Ironic, maybe. But it sets the stage for a future article: public key cryptography — where sender and recipient no longer need to share a secret in advance.
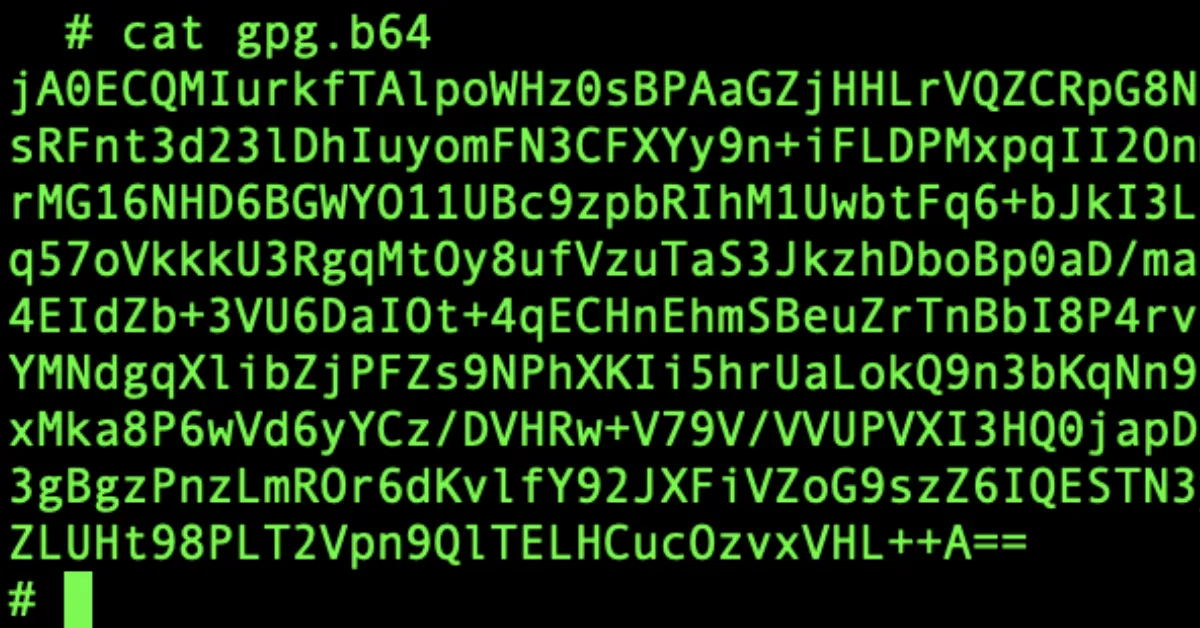
🌀 Bonus Round: Base64 of Encrypted Message
Finally, I encoded the encrypted message in Base64.
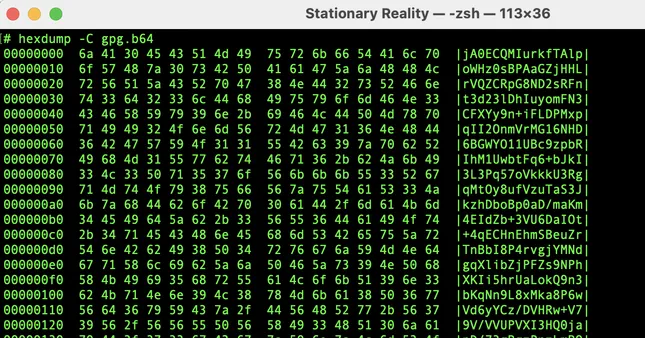
It looks just like the earlier base64 version — but this one is actually encrypted.
Same wrapping. Very different contents.
🛠️ How to Use GPG on the Command Line
Here’s how you can encrypt and decrypt local files with a passphrase:
# Encrypt a file (symmetric mode)
gpg -c secret.txt
# Decrypt the file
gpg -d secret.txt.gpg > decrypted.txt
It’ll prompt you to create or enter a passphrase. That’s it.
🚀 GPG As a Building Block (Beyond Files)
Like most open-source tools, GPG gets interesting when paired with other software.
Here are just a few of the ways it’s used in real-world workflows:
| 🧩 Use Case | 🔍 Description |
|---|---|
| 📬 Encrypted Email (CLI & GUI) | Sign and encrypt messages with [Thunderbird + Enigmail] or mutt + GPG. |
| 📁 Virtual File Systems | Used behind the scenes in [gocryptfs] or [encfs] for dynamic encrypted mounts. |
| 📋 Secure Clipboard / Notes | Tools like pass (Unix password manager) use GPG to encrypt secrets on the fly. |
| 💬 Encrypted System Alerts | Some sysadmins use GPG+sendmail or Discord bots to deliver encrypted alerts. |
| 🌐 Package Signing | Many Linux distros and dev tools use GPG to verify package authenticity. |
Want to test it out? Try
gpg -c myfile.txt— and feel the shift from visible to hidden.
🔜 Coming Up Next…
🔐 VeraCrypt
A tool purpose-built for encrypted containers and entire volumes, ideal for protecting large sets of data — even bootable systems.
Stay tuned.