🌐 DNS: The Internet’s Address Book
DNS (Domain Name System) translates website names like example.com into IP addresses like 93.184.216.34. Every time you visit a site, your device makes a DNS request to find out where to connect.
But here’s the issue:
Most DNS queries are still unencrypted.
That means even if the site itself uses HTTPS, your DNS requests can expose which domains you’re visiting.
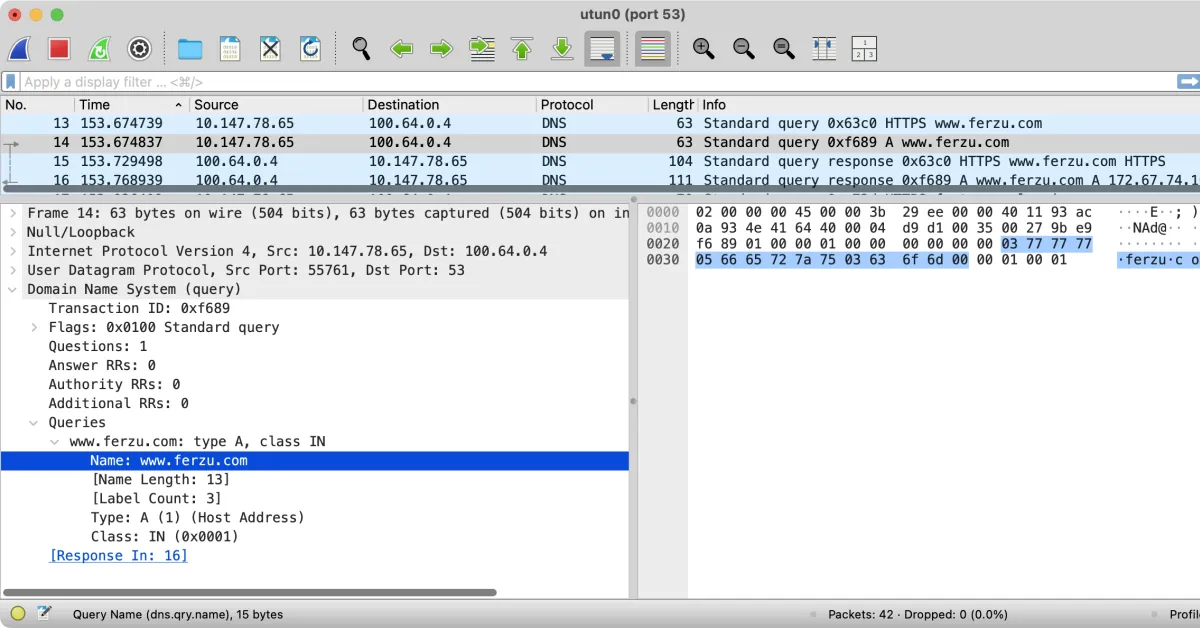
🧪 DNS Leaks in Action: A Wireshark Capture
While testing encrypted web traffic, I noticed something troubling: Safari on macOS was leaking DNS queries in the clear—even over a VPN.
Wireshark showed the full domain name of the website I was visiting, unencrypted, visible to anyone watching the connection.
This wasn’t a mistake in my VPN. It was a misconfiguration.
➡️ Librewolf, by contrast, did not leak anything—because I had explicitly configured it to use encrypted DNS.
🕵️♂️ Who Sees What?
Let’s break down who sees what depending on your setup:
- Your ISP: Knows your DNS queries and destination IPs — unless you use a VPN.
- Your VPN provider: Sees destination IPs, not the site names — unless DNS leaks.
- Your DNS provider: Sees the site names you resolve — even if encrypted, unless you trust them.
This brings us to one of the most important privacy concepts:
Anonymity = They know what you’re doing, but not who you are.
Privacy = They know who you are, but not what you’re doing.
🔄 Layered Privacy: Spread the Trust
The best strategy is to fragment trust:
- Use a VPN to hide traffic from your ISP.
- Use an encrypted DNS provider to hide queries from your VPN.
- Use browsers like Librewolf that support DNS over HTTPS (DoH).
This way, no single entity sees the full picture.
📶 Types of Encrypted DNS
There are three main standards:
- DNS over HTTPS (DoH): DNS traffic is sent over regular HTTPS (TCP 443). Supported by most modern browsers.
- DNS over TLS (DoT): Uses a dedicated port (853) and encrypts DNS using TLS. Supported at OS level in some systems.
- DNSCrypt: An older but still used protocol with built-in encryption and integrity checks.
🗺️ Recommended Encrypted DNS Providers
| Provider | Protocols Supported | Open Source? | Notes |
|---|---|---|---|
| LibreDNS | DoH, DoT | ✅ Yes | Focus on privacy, no logging |
| Mullvad DNS | DoH, DoT | ✅ Yes | Runs on secure VPN infrastructure |
| NextDNS | DoH, DoT | ✅ Partial | Customizable, strong policies |
| Quad9 | DoH, DoT | ✅ Yes | Malware filtering, privacy-first |
| Cloudflare | DoH, DoT | ❌ No | Fast, trusted by some, logs minimal |
For maximum trust, stick with providers that are:
- Open source
- Log-free
- Transparent about infrastructure
🧩 It’s Not Just Technical — It’s Personal
Seeing DNS queries in plain text is like watching someone’s browser history scroll by.
No one wants to broadcast their internet history, but that’s exactly what happens when DNS is left unencrypted.
Use encrypted DNS. Configure your browser. Double-check your OS. And never assume the default is private.